Make User objects work like userProxy objects
If, for some reason, your application can only lookup objects with ObjectClass equal to “user” you can change the user class so that it’s more like the userProxy class.
First install ADLDS on the machine that will host the instance:
| |
Now you can create a modified version of the MS-User.LDF that is included with AD-LDS:
| |
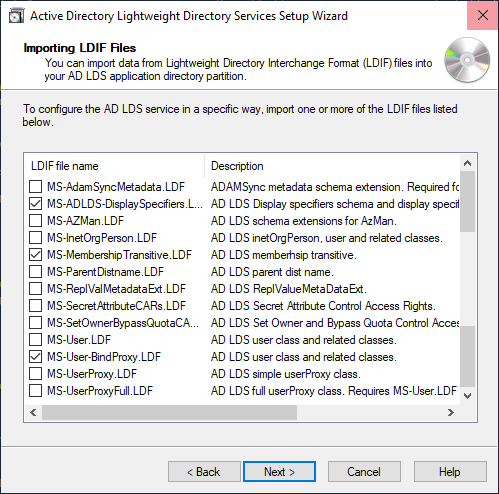
When you run the AD-LDS installer choose the new MS-User-BindProxy.LDF instead of the MS-User.LDF:
Move AD-LDS FSMO Roles
First validate that replication is healthy on the AD-LDS server:
| |
Find the FSMO role holder using dsmgmt:
PS C:\> dsmgmt
dsmgmt: roles
fsmo maintenance: connections
server connections: connect to server localhost:389
Binding to localhost:389 ...
Connected to localhost:389 using credentials of locally logged on user.
server connections: quit
fsmo maintenance: select operation target
select operation target: list roles for connected server
Server "localhost:389" knows about 2 roles
Schema - CN=NTDS Settings,CN=SERVERNAME$InstanceName,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,CN={00000000-0000-0000-0000-000000000000}
Naming Master - CN=NTDS Settings,CN=SERVERNAME$InstanceName,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,CN={00000000-0000-0000-0000-000000000000}
select operation target: quit
fsmo maintenance: quit
dsmgmt: quit
Change the FSMO role holder (input shown in red):
PS C:\> dsmgmt
dsmgmt: roles
fsmo maintenance: connections
server connections: connect to server targetserver:389
Binding to targetserver:389 ...
Connected to targetserver:389 using credentials of locally logged on user.
server connections: quit
fsmo maintenance: transfer naming master
Server "targetserver:389" knows about 2 roles
Schema - CN=NTDS Settings,CN=SERVERNAME$InstanceName,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,CN={00000000-0000-0000-0000-000000000000}
Naming Master - CN=NTDS Settings,CN=SERVERNAME$InstanceName,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,CN={00000000-0000-0000-0000-000000000000}
fsmo maintenance: transfer shema master
Server "targetserver:389" knows about 2 roles
Schema - CN=NTDS Settings,CN=SERVERNAME$InstanceName,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,CN={00000000-0000-0000-0000-000000000000}
Naming Master - CN=NTDS Settings,CN=SERVERNAME$InstanceName,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,CN={00000000-0000-0000-0000-000000000000}
fsmo maintenance: quit
dsmgmt: quit